-
Gallery of Images:
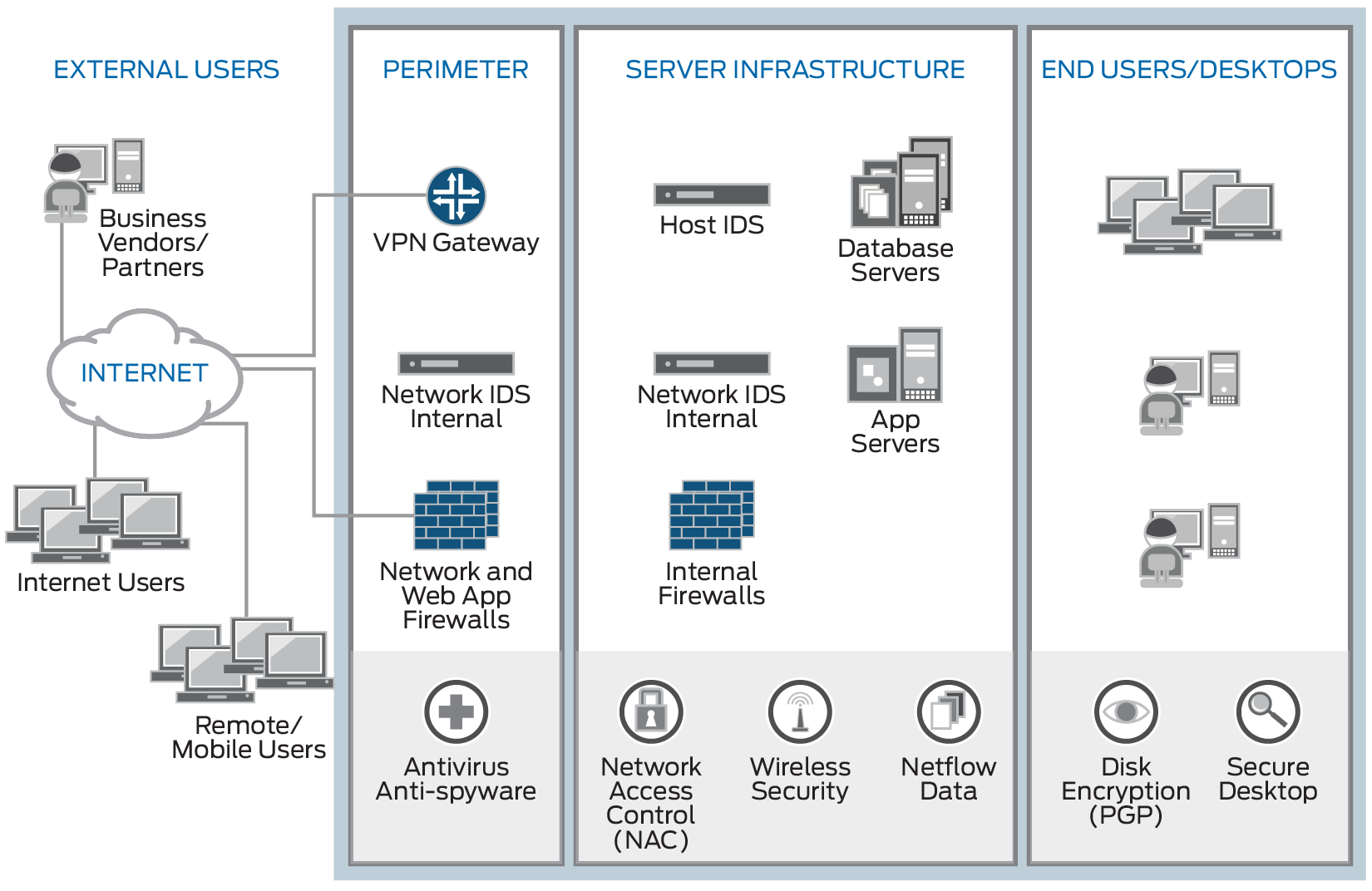
-
Importance of Data Security in Master Data Management. Intelligent datadriven disruption is at the forefront of corporate strategies. Using data to capture new opportunities requires a strategic focus on businesscritical data. Our Proactive Data Security service enables organisations to outsource their data security and compliance management resulting in benefits such as generating revenue and providing a quality service, reducing your risk, whitelabeled services, bestin. Best Data Security Software Data security software protects and encrypts data, directories, and systems from threats, hacks, and mechanical failure. Companies will use data security software to protect sensitive information about their business, clients, and customers. Data management refers to an organization's management of information and data for secure and structured access and storage. Data management tasks include the creation of data governance policies, analysis and architecture; database management system (DMS) integration; data security and data source identification, segregation and storage. The Vormetric Data Security Platform makes it efficient to manage dataatrest security across your entire organization. Built on an extensible infrastructure, Vormetric Data Security Platform products can be deployed individually, while sharing efficient, centralized key management. Explore the world of SAP security, data protection, and privacy Previous. continuous security monitoring, and 247 security response management for protection inside and outside the company. Learn more about cybersecurity; Data Protection. Thirdparty data security best practice steps provide you a framework by which to assess and address potential data risks posed by vendors. CONFIDENTIAL Page 2 GLOBAL DATA SECURITY AND INTERNET CREDENTIALS MANAGEMENT AGREEMENT (ICMA) Version. 1 Business Partner Intranet Authentication (BPIA) means provision of digital certificates to 3rd Job description for Data Security Manager. Including requirements, responsibilities, statistics, industries, similar jobs and job openings for Data Security Manager. 2017 Ventana Research Award Winner For Digital Innovation in Human Capital Management Category. Data Security Manager: Manages and guides the. An information security management system (ISMS) is a set of policies and procedures for systematically managing an organization's sensitive data. The goal of an ISMS is to minimize risk and ensure business continuity by proactively limiting the impact of a security breach. Sophistication of the data security policy definition and process management capabilities. Organizations typically have multiple policies for different types of data and multiple processes to manage data and respond to data loss related events. Strong encryption, DLP, policydriven security, management of Apple FileVault and Microsoft BitLocker native encryption, and data protection for cloud storage combine with a centralized management platform in our most robust data protection suite. The enterprise security management landscape is everchanging in a mobilefirst, cloudfirst world. Meet these challenges headon with an identitydriven approach and the latest security technologies for users, devices, apps, and data. Managing Data Center Security written by John Laskey April 2, 2014 In February 2014 DCN, I ended my retrospective on data center security by highlighting two standards, ISO (i. , for an information security management system, or ISMS) and ISO (i. , for a business continuity management system, or a BCMS). Vormetric Data Security Manager centralizes encryption key and policy management to remove data security deployment and operational complexity. Data Management for Drug Discovery Delivers data security intelligence so organizations can understand sensitive data risks and vulnerabilities. Protects unauthorized access to and disclosure of sensitive, private, and confidential information. A security policy is a comprehensive document that defines a companies methods for prevention, detection, reaction, classification, accountability of data security practices and enforcement methods. Fortunately, Gemalto's proven SafeNet twofactor authentication, encryption, and enterprise key management solutions turn any cloud environment into a trusted and compliant environment by solving the critical challenges of data governance, control, and ownership no matter where you store your data. ObjectiveThe information security management auditassurance review will: Provide management with an assessment of the effectiveness of the information security management function Evaluate the scope of the information security management organization and determine whether essential security functions are being addressed effectively Informing Science Data Security Volume 5 No 1, 2002 Paper Editor: Lech Janczewski Data Security Management in Distributed Computer Systems At Box, we're dedicated to bringing secure, centralized and cloudnative content services to organizations all over the world. We embed security and resilience not only into our products, but into the very fabric of our enterprise. With Box, you can easily manage file access and sharing policies, as. Unify endpoint, network, and data security management with our centralized security management system, available on premises or via the cloudincluding AWS. Gain endtoend visibility, slash incident response times, and reduce the cost and complexity of managing risk and security. ASUS Data Security Manager is a program developed by ASUS. The most used version is, with over 98 of all installations currently using this version. It adds a background controller service that is set to automatically run. Delaying the start of this service is possible through the service manager. The software is designed to connect. management, security monitoring, and au diting. These are discussed only in relation to internal security mechanisms. Neither have we attempted a treatment of privacy and the law. Our objective is simply an overview of four areas of security research. A key data security technology measure is encryption, where digital data, softwarehardware, and hard drives are encrypted and therefore rendered unreadable to unauthorized users and hackers. One of the most commonly encountered methods of practicing data security is the use of authentication. Data Protection Officers, IT Managers, Compliance Officers, Corporate Security Officers, legal advisers, persons responsible for risk management, and others. View training courses by: Subject Area Anti Money Laundering Bribery Compliance Data Protection Data Security Environmental Information Freedom of Information Human Resources Records. Time Data Security Founded in 1989, Time Data Security (TDS) Ltd is committed to the development of innovative, future proof secure access solutions for everyone. This commitment to developing stateoftheart software security ensures you benefit from a safe. Windows 10 changes the game for business IT security, protecting identities, devices and data with advanced capabilities. Get truly intelligent security. Windows 10 changes the game for business IT security, protecting identities, devices and data with advanced capabilities. Includes comprehensive security lifecycle management for security. The data management protocol consists of two steps: A data management section in the research proposal in which the researcher should answer a number of short questions; A data management plan that must be submitted after the proposal has been awarded funding. Learn about working at Data Security Management (Tate Int. See who you know at Data Security Management (Tate Int. ), leverage your professional network, and get hired. ISOIEC: 2013 (ISO ) is the international standard that describes the requirements for an ISMS (information security management system). Avoid the financial penalties and losses associated with data breaches. Given the state of todays security systems, most organizations are a long way from using these types of advanced technologies for security management. Anixters Risk Management is a sixlayered approach to Data Center Security. To understand more about these layers, attend relevant webinars or download insi Data security means protecting digital data, such as those in a database, from destructive forces and from the unwanted actions of unauthorized users, such as a cyberattack or a data breach. Disk encryption refers to encryption technology that encrypts data on a hard disk. The ORD pilot aims to improve and maximise access to and reuse of research data generated by Horizon 2020 projects and takes into account the need to balance openness and protection of scientific information, commercialisation and Intellectual Property Rights (IPR), privacy concerns, security as well as data management and preservation questions. Many Harvard faculty, staff and student members engage in research that involved the collection or use of identifiable private information. Federal law and Harvard policy provide specific guidance or protecting identifiable research information. Data is the lifeblood of any company, no matter the industry or size. And as the workforce evolves, data is being used anywhere, at all times, which leaves it vulnerable to new risks. As an endpoint pioneer, Dell Data Security has been creating innovative solutions proven to. Empower end users and secure sensitive data across your enterprise with Dell Data Security Solutions. Mozy solutions offer military grade security and world class data management, all from storage leader DellEMC. MozyEnterprise Cloud Backup Datasheet MozyPro Cloud Backup Datasheet MozyEnterprise Security Datasheet MozyPro Security Datasheet Information Security Management aims to ensure the confidentiality, integrity and availability of an organization's information, data and IT services. ITIL Security Management usually forms part of an organizational approach to security management which has a wider scope than the IT Service Provider. Overcome HIPAA Security Challenges Learn how online forms can help you safely collect patient data and avoid security breaches. The Key to Successful Data Security Management. HIPAA data breaches are an alltoo common occurrence today. ; 7 minutes to read Contributors. In this article security role enables an associated user to have full importexport capabilities in the Data management workspace. This security role has two security duties for each of the five data entity categories that are assigned to it. Protiviti provides data security and privacy management solutions. Protivitis riskbased approach is focuses on creating a secure environment. Our solutions include: data governance, data classification, data leakage, encryption storage strategy, privacy management, vendor management, and few more. Ensure the availability, integrity, and confidentiality of your business information. Trend Micro gives you a full range of data loss prevention and encryption solutions that encrypt, control, and protect your private data and intellectual property from endpoint to cloud. Data Center Security: Server Advanced Security hardening and monitoring for private cloud and physical data centers with support for Docker containers. Agentless Docker container protection with full application control and integrated management ISOIEC family Information security management systems. businesses will handle increasingly large amounts of data. The security of this information is a major concern to consumers and companies alike fuelled by a number of highprofile cyberattacks. Integrated data management (IDM) is a tools approach to facilitate data management and improve performance. IDM consists of an integrated, modular environment to manage enterprise application data, and optimize datadriven applications over its lifetime. Free Download Acer eDataSecurity Management 2. 8 r4354 A reliable and powerful software solution that enables Aces users to quickly encrypt and dec Data management from SAS is an industryleading solution built on the SAS Platform that helps you improve, integrate and govern your data. Benefits Boost productivity and work more efficiently. Read about 10 data security management tips to help you avoid a data breach that could cost your business thousands in fees and lost business. Acer eDataSecurity Management, tlcharger gratuitement. Acer eDataSecurity Management: Acer eDataSecurity Management est un utilitaire de cryptage de fichiers ayant la capacit de protger les fichiers de l'accs des personnes non autorises au moyen d'algorithmes de chiffrement avancs et l'utilisation de mots de passe..
-
Related Images:











